MITMf Framework for ManInTheMiddle attacks. 私 の 世界

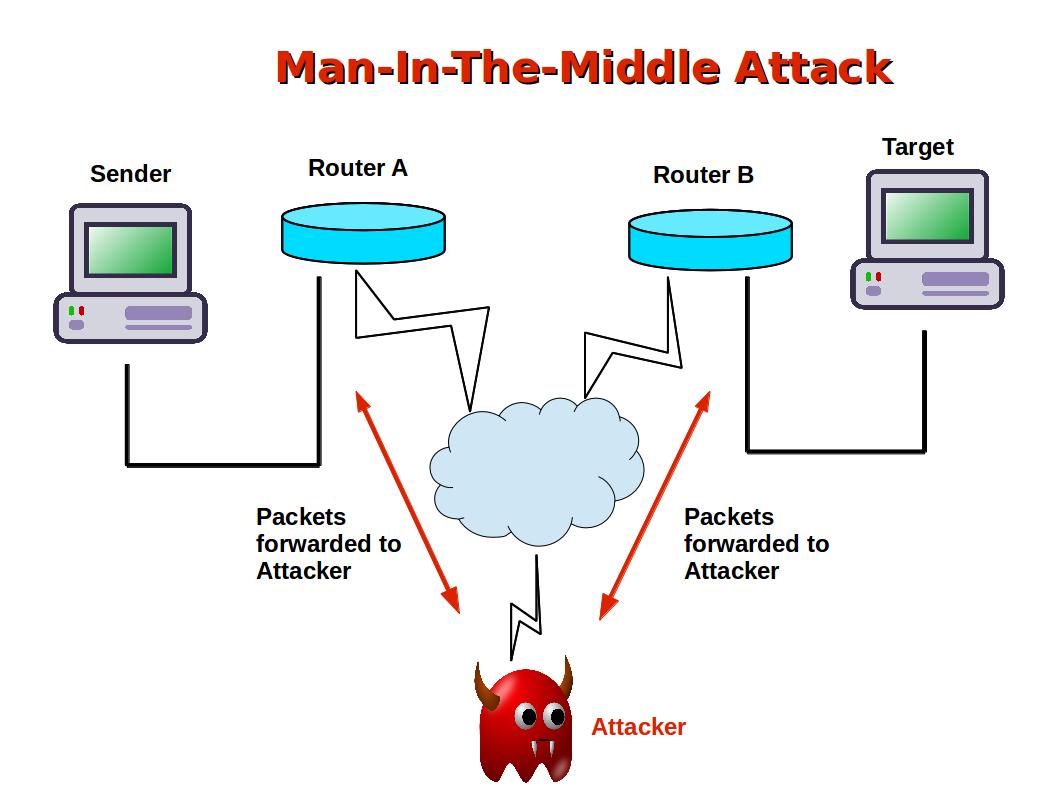
What is a Man-in-the-Middle Attack? Man-in-the-Middle (MITM) attack is a cyber attack where a cybercriminal intercepts data sent between two businesses or people. The purpose of the interception is to either steal, eavesdrop or modify the data for some malicious purpose, such as extorting money.
What is the ManInTheMiddle (MITM) attack? The Security Buddy

In cryptography and computer security, a man-in-the-middle [a] ( MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two parties. [9]
Attaque Man in the Middle (MITM) malekal's site

A man-in-the-middle (MITM) attack is a form of cyberattack in which criminals exploiting weak web-based protocols insert themselves between entities in a communication channel to steal data.. None of the parties sending email, texting, or chatting on a video call are aware that an attacker has inserted their presence into the conversation and that the attacker is stealing their data.
L'attaque maninthemiddle explication et omment s'en protéger

Attaque Man in the Middle (MITM) Une attaque de l'homme du milieu désigne un modèle de cyberattaque dans lequel un cybercriminel installe, physiquement ou logiquement, un système contrôlé entre le système de la victime et une ressource Internet qu'elle utilise. L'objectif de l'attaquant est d'intercepter, de lire ou de manipuler.
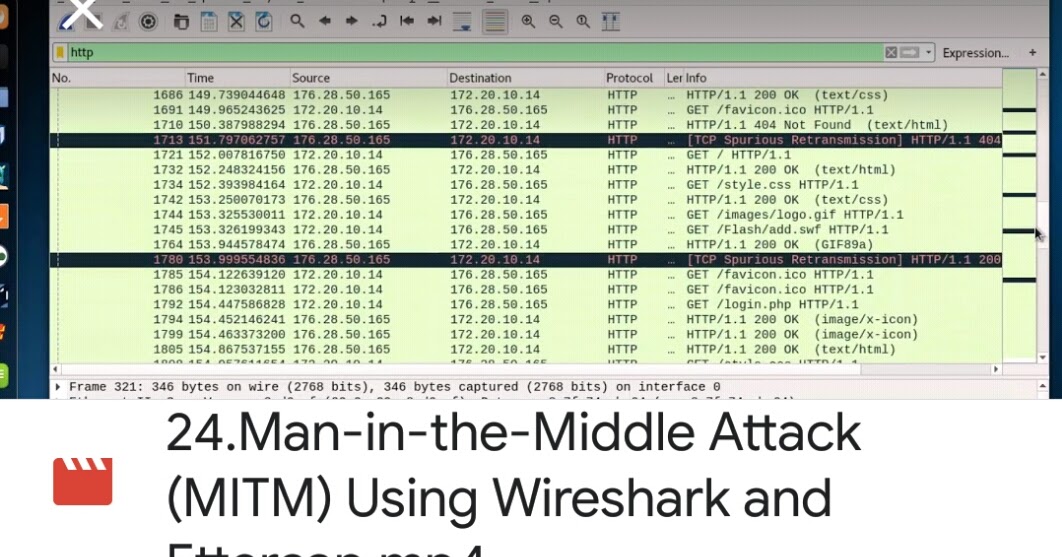
ManintheMiddle Attack (MITM) Using Wireshark and Ettercap
A man-in-the-middle attack intercepts and redirects your internet connection. Image source: Author. How to detect a MITM attack: 3 signs and symptoms.
¿Qué es un ataque ManintheMiddle (MITM)? Definición y prevención

A Man-in-the-Middle attack requires the attacker to place himself between two communicating parties and relaying messages for them, while the parties believe they are communicating with each other directly and securely. The attacker can then monitor and possibly change the contents of messages. MitM concept is not limited to computer security.
Computer Security and PGP What is a ManInTheMiddle Attack
The Middle East has teetered on the edge of wider conflict since Hamas attacked Israel on Oct. 7, an attack Israel says killed 1,200 people and took another roughly 250 hostage. Israel's.
Attaque Man in the Middle (MITM)

L' attaque de l'homme du milieu ( HDM) ou man-in-the-middle attack ( MITM ), parfois appelée attaque du monstre du milieu ou monster-in-the-middle attack 1, 2 ou attaque de l'intercepteur, est une attaque qui a pour but d'intercepter les communications entre deux parties, sans que ni l'une ni l'autre puisse se douter que le canal de.
ManIntheMiddle Attack einfach erklärt + Tools / HTTPs
Man-in-the-Middle Attack Types A man-in-the-middle attack can come in many shapes, yet the most common are the following: 1. IP spoofing The Internet Protocol Address (IP) refers to a numerical label that is assigned to each device that connects to a computer network that uses the Internet Protocol for communication.
What is Man in the Middle Attack? Types of Man in the Middle Attack

A man-in-the-middle attack is a type of eavesdropping attack, where attackers interrupt an existing conversation or data transfer. After inserting themselves in the "middle" of the transfer, the attackers pretend to be both legitimate participants. This enables an attacker to intercept information and data from either party while also sending.
ManintheMiddle Attacks explained, defined

During a man-in-the-middle (MitM) attack, threat actors gain access to a communication channel between legitimate parties (such as users, applications or network devices), allowing the perpetrators to view, delete or modify any message sent.. Man-in-the-middle attack mechanism. There are different ways to gain access to a communication channel. For example, an unscrupulous post office employee.
Qu'estce qu'une attaque ManintheMiddle (MiTM)
Quick Links. A man-in-the-middle (MITM) attack occurs when someone sits between two computers (such as a laptop and remote server) and intercepts traffic. This person can eavesdrop on, or even intercept, communications between the two machines and steal information. Man-in-the-middle attacks are a serious security concern.
Qu'estce qu'une attaque maninthemiddle (MITM)

The man in the middle. The intended recipient or application. One person - the victim - sends sensitive data online, such as an email. Then, there is an intended recipient - an application, website, or person. Between them, we have the "man in the middle.". This is the malicious actor who finds vulnerabilities, allowing them to watch.
ManintheMiddle attack schematic Download Scientific Diagram

Appelé en français « attaque de l'homme du milieu », une attaque man-in-the-middle est une cyberattaque s'immisçant entre 2 entités communicantes de manière à intercepter ou altérer.
What is ManintheMiddle Attack MITM Attack Explained Edureka Cybersecurity Rewind 4

Free trial. A man-in-the-middle attack (MITM attack), sometimes known as a person-in-the-middle attack, is a cyber attack where an attacker relays and possibly alters communication between two parties who believe they are communicating directly. This allows the attacker to intercept communication, listen in, and even modify what each party is.
Performing Man in the Middle Attack on HTTPS Powered Environments Lucideus Research by
Examinons les différents types d'attaques MITM. 1. Piratage d'e-mails. Comme son nom l'indique, dans ce type d'attaque, les cybercriminels prennent le contrôle des comptes de messagerie des banques, des institutions financières ou d'autres entreprises de confiance qui ont accès à des données sensibles et à de l'argent.
.